If I give you the code of an android app and ask you to provide me information regarding the android app like minSdkVersion, targetSdkVersion, permissions, configurations, almost anyone who knows how to code an android app would provide it to me in a few minutes. But what if I gave you an android apk file and then ask you to answer for the same 🤔 Its tricky if you try to think at the very first instance.
I actually ran into such a situation and even though I had known aapt tool for a long time, it didnot hit my head the very first instance when I had to get the permissions declared inside the apk. It was clear I needed to brush up the concepts and follow an efficient approach. This blog post will explain how to do so. Also helpful when you are trying to reverse lookup contents of any other app 🤓
Ok, the most common way to approach this problem has to be this one
Going with the definition of an APK
Android application package (APK) is the package file format used by the Android operating system for distribution and installation of mobile apps and middleware.
…APK files are a type of archive file, specifically in zip format packages based on the JAR file format, with .apk as the filename extension.

..hmm so its basically a ZIP format, so what I can do is rename the extension from .apk to .zip and I should be able extract the contents.
Cool, so we now see what the zip file contain and they are all available for inspection.

Well at this point you would think that you have got access to all files so you can give me all the information right away. Well not so quick Mr.AndroidDev 😬
Go ahead try and open up the AndroidManifest.xml in some text editor to check out its content. This is what you would get
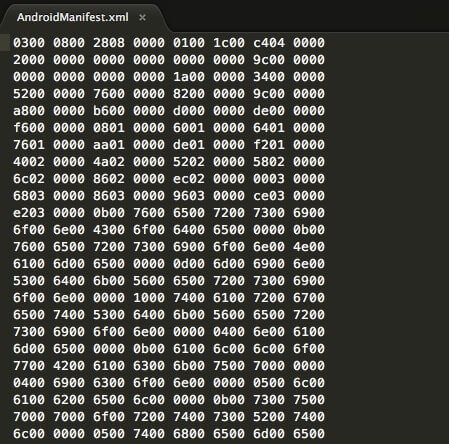
..what it basically means is that the AndroidManifest.xml isn’t in human readable format anymore. So your chances of reading basic information regarding the apk from the AndroidManifest.xml goes down the drain 😞
….
…
..
..Not really 😋 There are tools to analyze the Android APK and there is one which has been there since the very beginning.
I think its known to all the experinced devs but I am pretty sure a lot of budding as well as seasoned Android Devs have not even heard about it.
The tool thats available as part of the Android Build Tool is
aapt - Android Asset Packaging Tool
This tool can be used to list, add and remove files in an APK file, package resources, crunching PNG files, etc.
First of all, where exactly is this located 🤔
Good question, its available as part of build tools in your android sdk.
<path_to_android_sdk>/build-tools/<build_tool_version_such_as_24.0.2>/aapt
..ok so what can it actually do ? From the man pages of the tool itself
aapt list- Listing contents of a ZIP, JAR or APK file.aapt dump- Dumping specific information from an APK file.aapt package- Packaging Android resources.aapt remove- Removing files from a ZIP, JAR or APK file.aapt add- Adding files to a ZIP, JAR or APK file.aapt crunch- Crunching PNG files.
We are interested in aapt list and aapt dump specifically as these are what will help us provide apk information.
Lets find information that we are looking for directly from the apk by running the aapt tool on it.
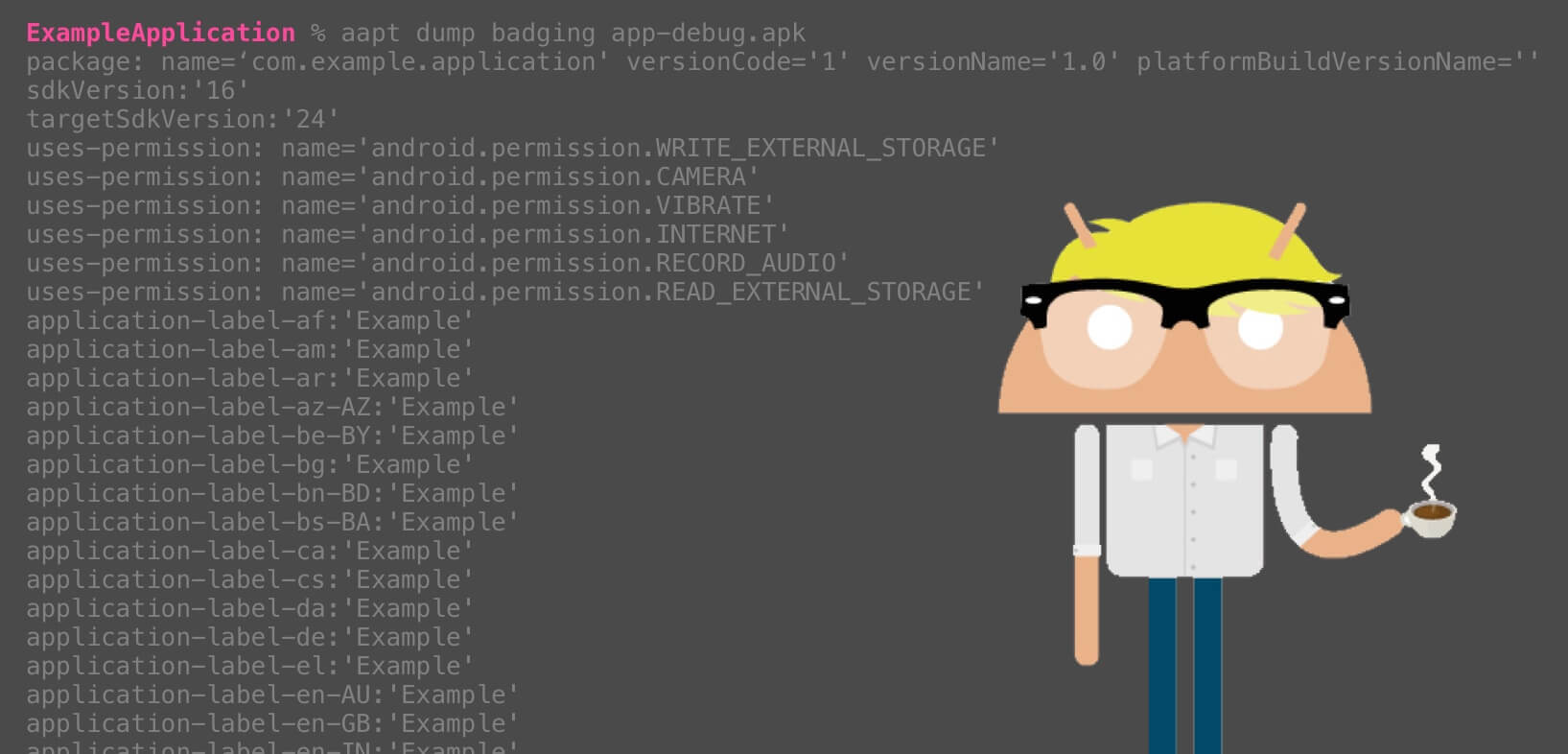
##### Get base information of the apk ```bash aapt dump badging app-debug.apk ```
> Result
|
|
##### Get list of permissions declared in the AndroidManifest of the apk ```bash aapt dump permissions app-debug.apk ```
> Result
|
|
##### Get list of configurations for the apk ```bash aapt dump configurations app-debug.apk ```
> Result
|
|
..also try out these
# Print the resource table from the APK.
aapt dump resources app-debug.apk
# Print the compiled xmls in the given assets.
aapt dump xmltree app-debug.apk
# Print the strings of the given compiled xml assets.
aapt dump xmlstrings app-debug.apk
# List contents of Zip-compatible archive.
aapt list -v -a app-debug.apk
.. as you can see you can easily get the information without even going through the process of unzipping the apk, but by using the aapt tool directly on the apk.
There is more that you can do , taking more info from the man pages of the aapt tool
|
|
..I will let you explore these on your own 🙂
Comment/Suggestions always welcome.
Got featured in AndroidWeekly Issue 224, thank you for the love
If you would like to get more of such android tips and tricks, just hop onto my Android Tips & Tricks github repository. I keep updating it constantly.
Keep on crushing code!🤓 😁